When referencing incident response (IR), it can be instinctive to conjure up images of firefighting, focused on reactive action taken to quickly respond to and handle an active security incident during what is usually a high-pressure, high-stakes situation. We are all familiar with the stories of ever-evolving adversaries wreaking immediate (or delayed) havoc to an organization’s business operations, and causing lasting detrimental impact to their reputation and bottom line.
What is Incident Response?
The National Institute of Standards and Technology (NIST) defines incident response (or incident handling) as “the mitigation of violations of security policies and recommended practices,” while SANS Institute defines incident handling as an “action plan for dealing with intrusions, cyber-theft, denial of service, fire, floods, and other security-related incidents.”
Incident Response Life Cycles
At first glance, the single-sentence glossary definitions above seem to underscore the reactive nature of incident response, highlighting a trigger event that leads to switching into action. Beyond that, NIST, SANS and ISO, for example, all publish an incident response life cycle to aid responders and their organizations. These life cycles provide a useful framework and approach to incident response, outlining phases of incident response and offering checklists to help ensure effective and efficient response.
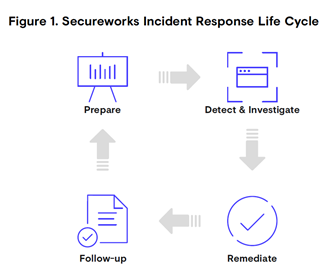
| NIST SP 600-61 r2 | SANS | ISO | Secureworks® |
| Preparation | Preparation | Prepare | Prepare |
| Detection & Analysis | Identification | Identify | Detect & Investigate |
| Containment, Eradication & Recovery | Containment | Assess | Remediate |
| Eradication | Respond | ||
| Recovery | |||
| Post-incident activity | Lessons Learned | Learn | Follow-up |
What Incident Response Life Cycles Teach Us
An examination of the phases as set out in the table above highlights three things:
- The standard of choice may differ by organization and can be tailored to the specific needs of your organization or incident, but fundamentally, a quick mapping reveals an underlying similarity in best practice approach and the phases involved for complete response and recovery. Our own Incident Response team has combined their education and knowledge of best practice standards with real-world experience gathered from backgrounds spanning national, military, and organizational Computer Security Incident Response Teams (CSIRTs), as well as intelligence & law enforcement agencies, and collective knowledge gleaned from 1,400 incident response engagements conducted at Secureworks annually. They organize to help our customers around four phases outlined in the Secureworks IR Life Cycle.
- Not one of the life cycles ignores the incident response preparation phase and the importance of post-incident activity. In addition, if you consider the graphical depictions of these phases, it’s clear that the outputs of post-incident activity or follow-up act as inputs to preparation to help ensure ongoing improvement. The Secureworks team is passionate about leveraging lessons learned from Incident Response engagements to inform the wider cybersecurity community as well as incident readiness services and Secureworks® Taegis™ platform innovation.
- Ultimately, and to follow-on from the point above, to be effective and efficient at limiting damage, reducing stoppages, and improving recovery time, incident response requires an organized approach. To do so, the emphasis is on building out a response program that includes ongoing, proactive phases involving preparation and planning, as well as continuous ingest of lessons learned and proactively seeking opportunity for improvement.
Proactive Incident Response
Now that we’ve established the value of incident response life cycles to guide best practices - how do you prepare for an incident? What exactly does preparation entail? Download our white paper - From Reactive to Proactive: Keys to Shifting Your Cybersecurity Strategy.
For a deeper dive into what to consider as part of your incident response preparation read our 5-part blog series on the Top 5 Findings from Secureworks’ Proactive Incident Response Engagements.
Sources:
Computer Security Incident Handling Guide (nist.gov)Incident Handling Definition (sans.org)
Incident Response Process (sans.org)
ISO/IEC 27035-1:2016

