Every year, Secureworks® incident responders help customers contain and remediate hundreds of cybersecurity incidents. The insights and trends discovered during these incident response (IR) engagements can help organizations make smarter decisions about cybersecurity strategy and tactics. Although the threat landscape and incident details fluctuate, five takeaways from 2021 engagements remain relatively consistent.
Takeaway #1: Ransomware continues to drive the need for better threat detection.
Post-intrusion ransomware is consistently the top reason that organizations request Secureworks IR engagements. Cybercriminals are increasingly adopting “name-and-shame” tactics, pressuring victims to pay ransoms by threatening to publicly release stolen data. This approach goes beyond simply holding encrypted data hostage.
Organizations must improve their ability to quickly discover, identify, and neutralize threat actors who have accessed the network. The better the threat detection, the better the chances of mitigating a compromise before the threat actors deploy ransomware.
Takeaway #2: Vulnerable internet-facing systems are a common initial access vector (IAV).
In 2021, exploitation of vulnerabilities in internet-facing systems (also known as scan-and-exploit attacks) displaced credential-based attacks as the most common IAV observed in Secureworks IR engagements (see Figure 1). There could be various explanations for this shift: organizations are increasing implementation of multi-factor authentication (MFA) to protect credentials, threat actors have improved their ability to weaponize exploit code that the cybersecurity community publishes when vulnerabilities are publicly disclosed, or infrastructure is being built out more rapidly than organizations can secure it.
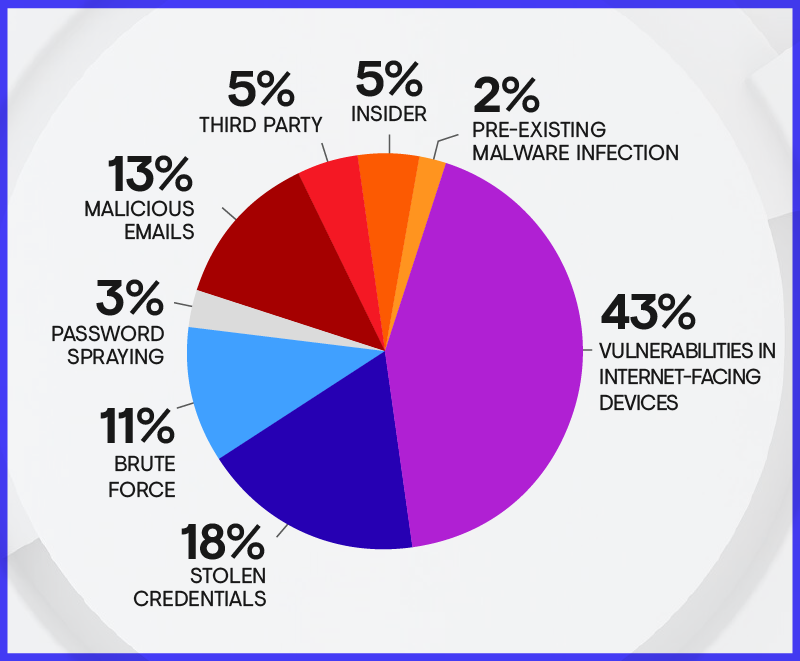
Figure 1. IAVs observed during Secureworks IR engagements in 2021. Due to rounding, the percentages may not add up to 100%. (Source: Secureworks)
Whatever the reason, one thing is clear: organizations must improve the speed and scale at which they can perform vulnerability assessments and remediations. In addition, given that no organization can patch every vulnerability in real time, it is vital to invest in vulnerability detection and response (VDR) technology. This technology enables organizations to prioritize patching activities based on the actual risk to the business.
Takeaway #3: Single-factor authentication is a liability.
Most of the IR engagements involving stolen credentials revealed threat actors authenticating to remote access solutions that did not enforce MFA. It is important for organizations to implement MFA across their environment and ensure that it is configured correctly. Organizations should also invest in rapid, reliable threat detection that is based on behavioral clues across all endpoints, network infrastructure, and cloud resources.
Takeaway #4: Email-based attacks continue to evolve.
Phishing and spearphishing emails are common and can include malicious links and attachments. Attacks that use third-party services such as social media, victims' personal webmail, and popular file-sharing sites for hosting malicious content can be particularly difficult to prevent because these services are not governed by enterprise security controls. As more employees work from home and access enterprise and personal resources on the same devices, it becomes easier for attackers to exploit personal contacts to gain enterprise access.
User education is a critical defense against email-based compromise. Training employees to recognize and report phishing attempts can limit the success of these attacks. The awareness can also help employees avoid compromise of their personal information.
Takeaway #5: Fundamentals are fundamentals for a reason.
Attackers often seek the path of least resistance. Organizations can prevent or quickly detect and remediate many incidents by implementing basic cybersecurity practices.
Secureworks incident responders provide tailored recommendations to affected organizations. Common recommendations address management of vulnerabilities, accesses, and logs. Figure 2 lists the most frequent recommendations provided during Secureworks IR engagements in 2021.

Figure 2. Most common recommendations provided during Secureworks IR engagements in 2021. (Source: Secureworks)

